Definition
Frequently, the only thing preventing hackers from compromising an entire private network is the perimeter firewall, a virtual boundary that protects against unauthorized external access. More firewalls can be spread throughout the network to strengthen the system’s security, but this approach doesn’t cover all vulnerable points, leaving many areas that hackers can exploit.
Micro-segmentation is an advanced networking security tool that offers fine-grained control over network traffic. It allows you to apply security policies that control inbound and outbound network traffic, not only on large portions of their networks but also on logical subdivisions, down to individual virtual machines (VMs) and VM groups.
With the primary goal of defining security controls and providing services to each segment, micro-segmentation restricts an attacker’s ability to exploit VM-to-VM traffic on the data center, even after the perimeter has been breached. Micro-segmentation is used to reduce your network’s attack surface, contain and minimize the impact of breaches, and increase regulatory compliance.
How does micro-segmentation work?
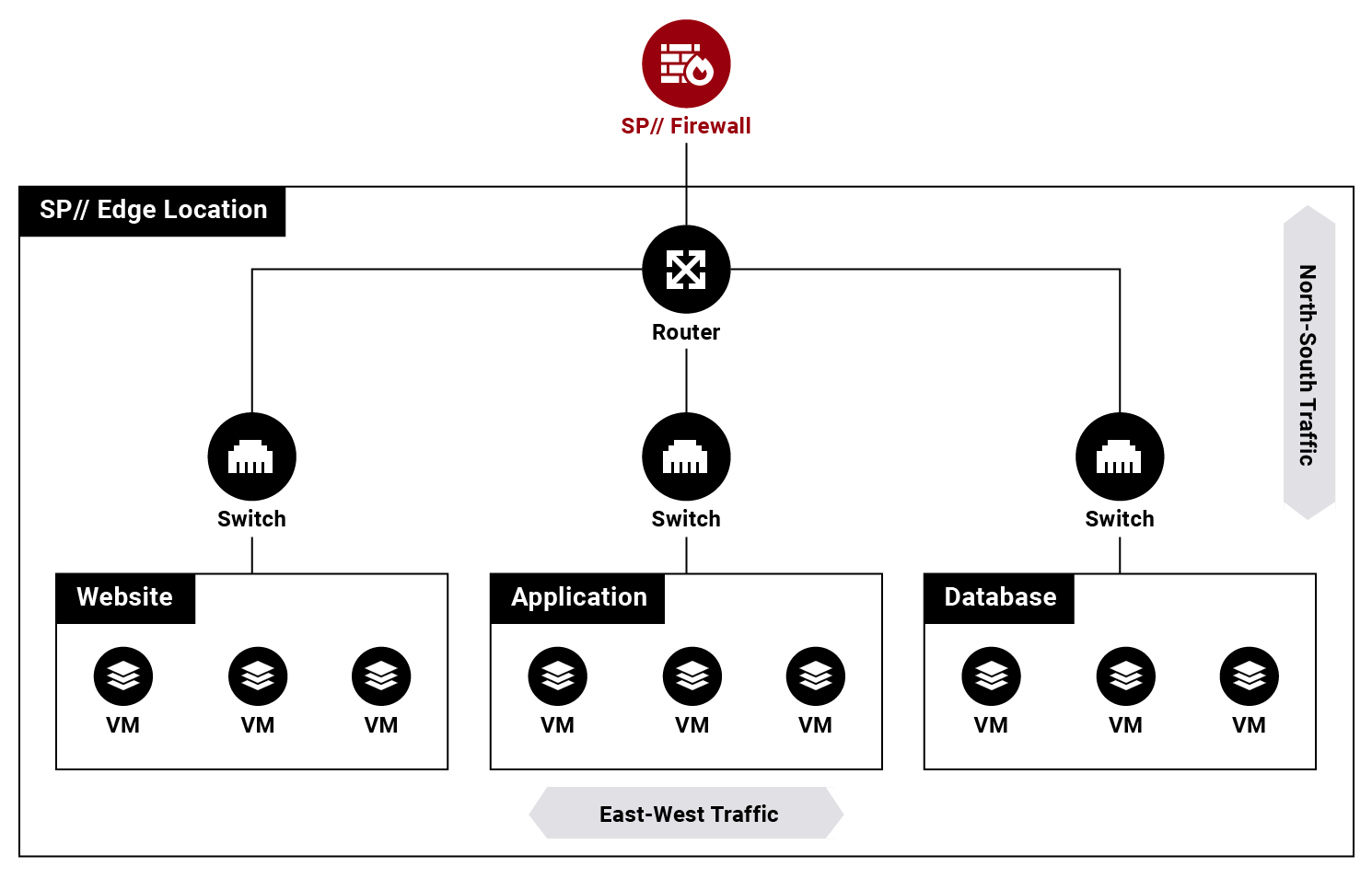
To understand how micro-segmentation works, you should start by turning your attention to north-south and east-west traffic.
A north-south traffic flow comes from outside the network boundary down to the subnet, the router, and the switch until it reaches the virtual machines and back again.
By contrast, east-west traffic is between different VMs within the same subnet with a point-to-point connection.
If an intruder manages to compromise a machine in the data center, it can exploit vulnerabilities that allow a VM to be attacked by another compromised VM. In a virtualized environment, this is called east-west movement VM jumping, which may contaminate an entire data center and its critical applications.
Micro-segmentation prevents VM jumping by bringing segmentation as close as possible to where the application resides. Each machine can’t “talk” to the outside world, even other VMs, without going through a firewall.
Therefore, the focus of micro-segmentation is not just protection but the containment of contamination. If one machine becomes compromised, local firewall rules within that segment will prevent the contamination from spreading to the rest of the data center.
Micro-segmentation achieves this using numerous techniques, including:
- Deploying flexible security policies in data centers and cloud systems using network virtualization
- Isolating each workload and securing it separately
- Breaking the network into smaller subnets
- Applying access-control lists (ACLs) to subnets, isolating machines on different network segments
Meanwhile, IT security personnel can work on solutions to remediate the situation as quickly as possible.
Micro-segmentation versus firewalls
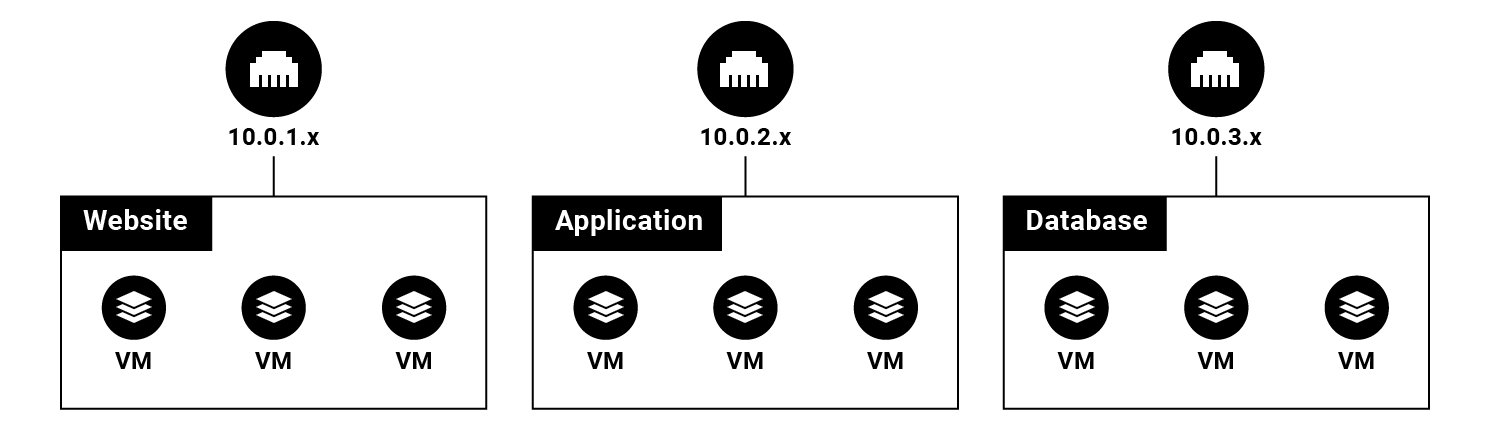
Imagine a simple network topology with a three-tier application connected to a router and three switches.
Each application tier involves multiple VMs and relies on a different switch. Those three switches operate on different IPs — for example, 10.0.1.x for the web tier, 10.0.2.x for the application tier, and 10.0.3.x for the database tier.
Traditionally, this architecture would have to run a separate firewall to enforce network security. A network perimeter firewall is placed as a secured boundary providing the primary defense of a data center’s private network.
Running a single firewall means that if a VM in the web tier must communicate with a VM on the app tier, the communication will follow this path:
- From the web tier switch to the router
- From the router to the firewall
- From the firewall back to the router
- From the router to the app tier switch
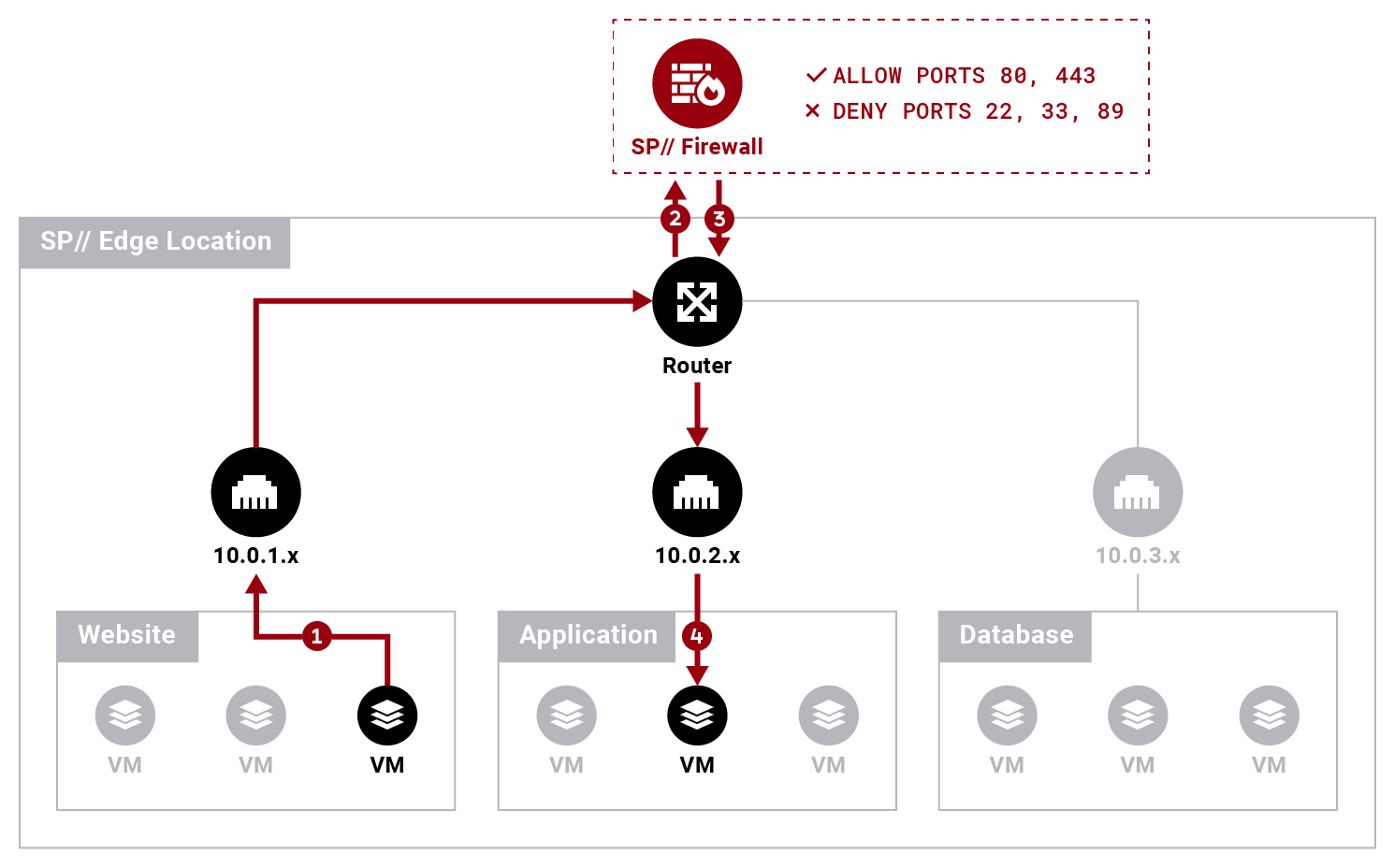
You can use the firewall to set up an ACL for your VM. An ACL is a list of permissions associated with a system resource. You can use it to configure rules for allowed or denied traffic. For example, you can:
- Allow incoming and outgoing traffic for ports 80 and 443.
- Deny incoming and outgoing traffic for ports 22, 33, and 89.
This is a simple example of what you could do with a traditional architecture, where a single firewall is responsible for enforcing the rules you’ve defined.
So what can you do with micro-segmentation?
You can scatter firewalls and firewall rules so that they apply directly to each VM, VM group, switch, department, or other logical segmentation you want to secure.
You can create an environment where each VM has its own complicated rules.
The previous diagram showed the traditional vision of firewall use, where you used an ACL to define which ports were allowed and denied for the VM on the web tier.
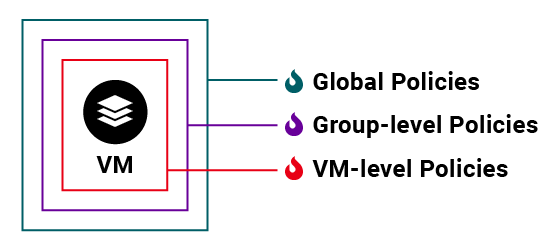
VM-level policies
With micro-segmentation, not only can you put a firewall on each VM, but you can also place firewalls in between VMs.
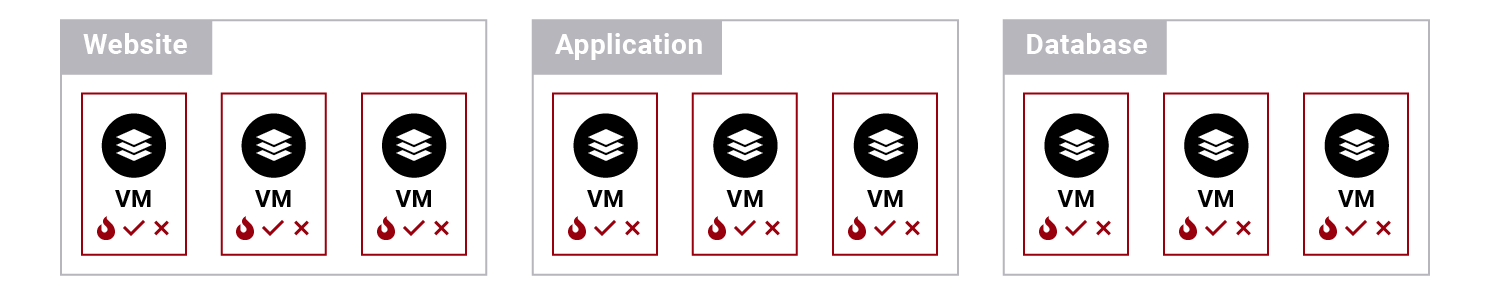
Group-level policies
You can have a group of VMs — for example, “finance group” — dedicated to a financial app and an ACL defining that this VM group on the application tier can communicate through port 80 with another VM in the web tiers.
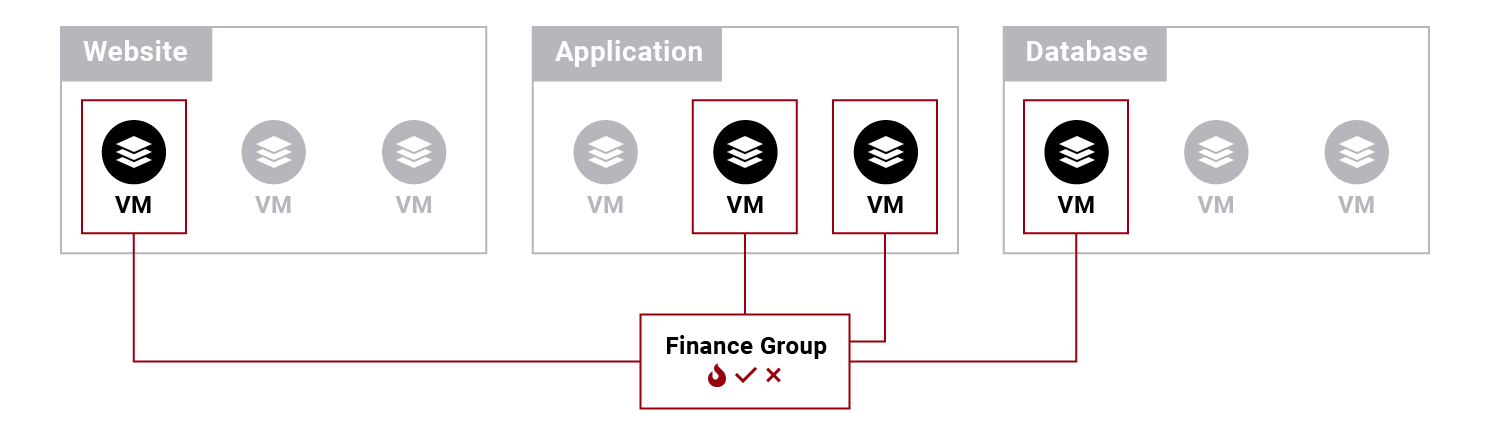
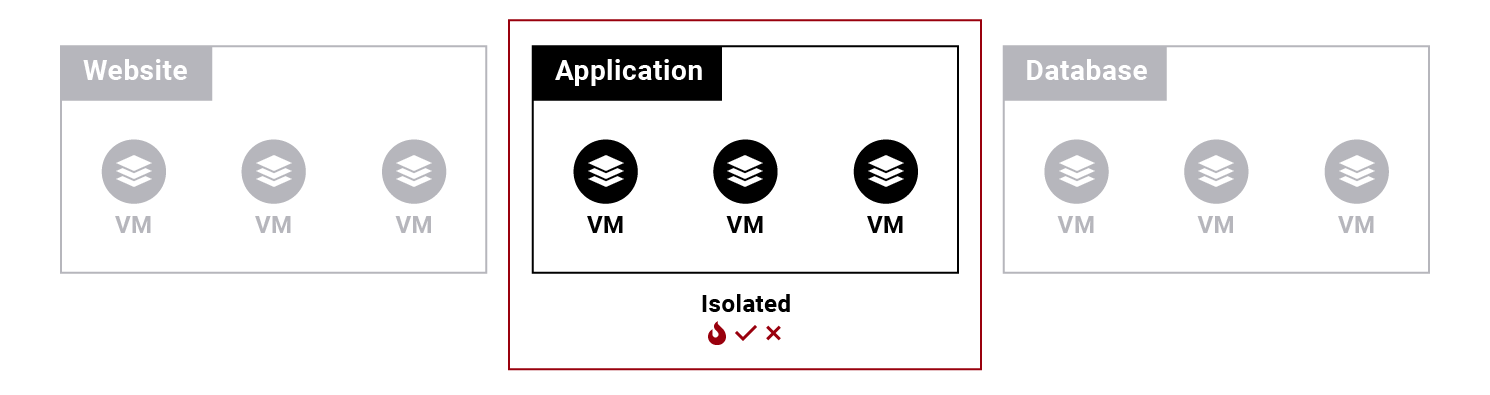
Global policies
You may create a global policy defining that the application tier is isolated.
Micro-segmentation allows you to apply many combined policies on the same VM. For example, a VM can be secured and restricted by its own firewall, the firewall on the group, the firewall on the switch, or the network perimeter firewall.
Benefits of Micro-Segmentation
There are several benefits to using micro-segmentation, including those listed below.
Reduces the Attack Surface
Recent years have seen a rapid increase in distributed architectures and heterogeneous environments. Solutions are deployed on-premises and to cloud data centers and mobile devices, to name a few environments. And the rise of the Internet-of-Things (IoT), Software-as-a-Service (SaaS), and virtualization created challenges that traditional perimeter firewall security can’t solve.
Micro-segmentation can address these challenges by helping enforce multi-layered and granular policies that work on different VMs, groups, and switch levels. This helps control east-west traffic and dramatically reduces the damage of a successful intrusion.
Protects Critical Applications
Micro-segmentation helps you gain better threat visibility and secure valuable assets across different platforms and environments, helping contain the spread of a threat emerging from a VM or service that has been hacked. This granular control allows you to limit the lateral traffic that might contaminate an entire data center and compromise high-value targets like critical applications.
Micro-segmentation allows network administrators to specify and adjust policies to fit critical applications. It provides consistent security across different platforms, delivers process-level granularity, and enables security policies to be implemented consistently in the data center and the cloud.
Meets Compliance with Regulators
Micro-segmentation helps organizations to strengthen their positions in the face of compliance mandates. With micro-segmentation, you can keep closer, detailed control over workloads that may contain sensitive data. It also supports proper security and data separation, which makes completing audits and ensuring document compliance easier.
Enhanced granularity means that regulatory officers can now scrutinize specific protocols from the network perimeter down to the process level, providing unprecedented levels of control for compliance.
With clearly defined application scopes and policies, cross-platform processes can be more easily auditable, with reduced risk of non-compliant usage. Systems subject to regulations can receive stricter policies that isolate them from the rest of the installation.
Key Takeaways
- Micro-segmentation prevents east-west attacks within the data center by bringing granular segmentation down to the VM level.
- Micro-segmentation helps reduce the attack surface, secure critical applications, and meet security compliance standards.
- Micro-segmentation policies are scalable and flexible enough to secure the entire network and its assets, providing modern security solutions for modern deployments.

